Lately, we've been seeing a lot of worms, and even some genuine viruses (*), coming into our network via USB memory sticks (aka "pen drives"). For those of us who remember the first MS-DOS viruses, which spread almost exclusively via diskette, it's rather nostalgic.
The culprit, of course, is Microsoft's desire to make things "simple" - meaning "automatic" - for Joe Sixpack; there's a fundamental incompatibility between a home entertainment system, which Windows has become, and an operating system for getting work done. (Here's a rule of thumb for you: any time you see stuff which starts without the user asking it to, look for malware to pop up in short order.)
These worms pretty much all reproduce the same way, at least in terms of how they jump to and from PCs. They have an AUTORUN.INF file and an executable of some kind. When you put the stick in the PC, Windows finds AUTORUN.INF "automagically". You can find documentation of some of the possible things which this file can do, but basically, the worm version will either run the executable immediately, or modify the Windows Explorer default behaviour so that the worm will run as soon as you open the stick by double-clicking on it. The executable will make a copy of itself and AUTORUN.INF on all the disk partitions and shared drive connections which it can see, and then open the root folder normally. (This takes a fraction of a second, but you won't notice it.) The executable will then sit around in memory and every time you insert a removable storage volume (such as another memory stick) or map a network drive, it will copy the worm "kit" to it.
Sometimes the executable will live in a fake \RECYCLED folder, which is quite clever because hardly anyone ever opens the recycle bin on a memory stick, and because the folder doesn't contain a real recycle bin structure, the worm will be safe, even if you empty the bin while the stick is in the drive.
Now, in theory you can prevent certain drive types from executing the contents of their AUTORUN.INF files using a registry value (NoDriveTypeAutoRun). But this is hard to do in practice. First, it's a per-user key, which in a corporate environment is harder to manipulate reliably than a per-PC key. Secondly, there are several bugs known for it. And thirdly, a little-known registry key called MountPoints2 contains cached information about every memory stick or other removable device which your PC has ever seen, and that overrides the NoDriveTypeAutoRun value if you insert a volume which the PC already knows about.
The only solution I could find from Microsoft is typically light and nimble: prevent all USB storage from running. This is fine if the aim is to stop people using memory sticks altogether, but didn't you just have a 4GB stick custom-printed for everyone in the company, and tell them to make their own backups on it?
Anyway, there seems to be a solution: a one-shot, quick way to prevent AUTORUN.INF files from being used on a PC, from any medium. My colleague and fellow low-budget Windows hacker Emin Atac thought up the idea, and I spent all of 15 minutes testing it. Now it's your turn (well, "the world is our beta site" works well enough as a corporate mantra for Microsoft).
All you do is to copy these three lines into a file called NOAUTRUN.REG (or anything.REG) and double-click it. Corporate network people can transform it into a script for their favourite command-line registry manipulator, or maybe make it a system policy thingy.
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf]
@="@SYS:DoesNotExist"
This hack tells Windows to treat AUTORUN.INF as if it were a configuration file from a pre-Windows 95 application. IniFileMapping is a key which tells Windows how to handle the .INI files which those applications typically used to store their configuration data (before the registry existed). In this case it says "whenever you have to handle a file called AUTORUN.INF, don't use the values from the file. You'll find alternative values at HKEY_LOCAL_MACHINE\SOFTWARE\DoesNotExist." And since that key, er, does not exist, it's as if AUTORUN.INF is completely empty, and so nothing autoruns, and nothing is added to the Explorer double-click action. Result: worms cannot get in - unless you start double-clicking executables to see what they do, in which case, you deserve to have your PC infected.
The only downside of this is that if you insert a CD with software on it, you have to explore it by hand to find the setup program. Of course, if that means your kids install less software, that could also be considered an upside.
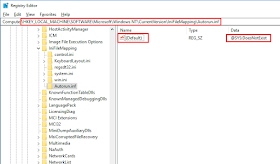
If you want to check that the registry settings of this hack are in place, open Regedit, walk down to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping, and you should see something like this:

(*) If you don't know the difference, Wikipedia is (probably) your friend.
The culprit, of course, is Microsoft's desire to make things "simple" - meaning "automatic" - for Joe Sixpack; there's a fundamental incompatibility between a home entertainment system, which Windows has become, and an operating system for getting work done. (Here's a rule of thumb for you: any time you see stuff which starts without the user asking it to, look for malware to pop up in short order.)
These worms pretty much all reproduce the same way, at least in terms of how they jump to and from PCs. They have an AUTORUN.INF file and an executable of some kind. When you put the stick in the PC, Windows finds AUTORUN.INF "automagically". You can find documentation of some of the possible things which this file can do, but basically, the worm version will either run the executable immediately, or modify the Windows Explorer default behaviour so that the worm will run as soon as you open the stick by double-clicking on it. The executable will make a copy of itself and AUTORUN.INF on all the disk partitions and shared drive connections which it can see, and then open the root folder normally. (This takes a fraction of a second, but you won't notice it.) The executable will then sit around in memory and every time you insert a removable storage volume (such as another memory stick) or map a network drive, it will copy the worm "kit" to it.
Sometimes the executable will live in a fake \RECYCLED folder, which is quite clever because hardly anyone ever opens the recycle bin on a memory stick, and because the folder doesn't contain a real recycle bin structure, the worm will be safe, even if you empty the bin while the stick is in the drive.
Now, in theory you can prevent certain drive types from executing the contents of their AUTORUN.INF files using a registry value (NoDriveTypeAutoRun). But this is hard to do in practice. First, it's a per-user key, which in a corporate environment is harder to manipulate reliably than a per-PC key. Secondly, there are several bugs known for it. And thirdly, a little-known registry key called MountPoints2 contains cached information about every memory stick or other removable device which your PC has ever seen, and that overrides the NoDriveTypeAutoRun value if you insert a volume which the PC already knows about.
The only solution I could find from Microsoft is typically light and nimble: prevent all USB storage from running. This is fine if the aim is to stop people using memory sticks altogether, but didn't you just have a 4GB stick custom-printed for everyone in the company, and tell them to make their own backups on it?
Anyway, there seems to be a solution: a one-shot, quick way to prevent AUTORUN.INF files from being used on a PC, from any medium. My colleague and fellow low-budget Windows hacker Emin Atac thought up the idea, and I spent all of 15 minutes testing it. Now it's your turn (well, "the world is our beta site" works well enough as a corporate mantra for Microsoft).
All you do is to copy these three lines into a file called NOAUTRUN.REG (or anything.REG) and double-click it. Corporate network people can transform it into a script for their favourite command-line registry manipulator, or maybe make it a system policy thingy.
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf]
@="@SYS:DoesNotExist"
This hack tells Windows to treat AUTORUN.INF as if it were a configuration file from a pre-Windows 95 application. IniFileMapping is a key which tells Windows how to handle the .INI files which those applications typically used to store their configuration data (before the registry existed). In this case it says "whenever you have to handle a file called AUTORUN.INF, don't use the values from the file. You'll find alternative values at HKEY_LOCAL_MACHINE\SOFTWARE\DoesNotExist." And since that key, er, does not exist, it's as if AUTORUN.INF is completely empty, and so nothing autoruns, and nothing is added to the Explorer double-click action. Result: worms cannot get in - unless you start double-clicking executables to see what they do, in which case, you deserve to have your PC infected.
The only downside of this is that if you insert a CD with software on it, you have to explore it by hand to find the setup program. Of course, if that means your kids install less software, that could also be considered an upside.
If you want to check that the registry settings of this hack are in place, open Regedit, walk down to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping, and you should see something like this:

(*) If you don't know the difference, Wikipedia is (probably) your friend.
This is exactly what I was looking for, I needed a way to disable just the AutoRun.inf functionality
ReplyDeleteThank you
Man, I'd been meaning to post that somewhere for ages! It took me hours of analyzing Procmon traces and Googling registry keys to figure out a way to accomplish this.
ReplyDeleteThe best part of disabling autorun in this manner is that CD audio and DVD Video will still autoplay when you insert the disc. Even those DVDs with silly autorun .exe files (or Sony's rootkitted CDs) will be properly recognized and opened up in your media player of choice! :)
I'm new at this, but does the second "@" sign inside the quote mark need to be there? When merged with the registry it leaves the @ sign there: @SYS:.....
ReplyDeleteYes, you need everything.
ReplyDeleteThe first "@" means "the magic, unnamed default value for this registry key. It's just an instruction to the REGEDIT4 loader.
The second @ is part of the final value which goes into the registry. It means "what follows is a pointer - follow it". We want Windows to follow the pointer and finish up at a dead end, where it will say, "OK, this entire INI file maps to nothing".
Going the other way around, I put nullified (no commands to execute hostile programs) AUTORUN.INF files on my flash disks with the RHS attributes on them, figuring that most worms can't run a check whether their AUTORUN.INF is ok. XD
ReplyDeleteThanks for this little piece of information. :)
Don't expect that to protect you too much when you put that stick in another PC. The worms I've seen are quite capable of deleting an "RHS" file. But so far I haven't seen one which also remembered to check that AUTORUN.INF wasn't a directory. So make a folder with that name and you might be protected somewhat (until a friend comes round and puts their stick in your PC...)
ReplyDeleteGreat tip. Unfortunately SanDisk U3 drives stop working after adding the register entry.
ReplyDeleteAs expected no software is autostarted, but manual launching of LaunchU3.Exe also fails. It looks like it uses AutoRun.Inf to store some settings. :-(
This is brilliant! Exactly what I want: The convenience of AutoPlay launching my own software, without the risks of AutoRun.inf launching something malicious.
ReplyDeleteIncidentally, if there is something legitimate that you want to launch when media is inserted (such as for a U3 drive, or to run your backup program when you connect the external drive), I'd recommend using USBVirusScan to respond to drive insertions. Make a little batch file that effectively says, "If it's my U3 drive, start the U3 LaunchPad."
For fuller control of what happens when a USB stick is inserted (especially with Autorun.inf files disabled), I wrote a small, free program called AutoRunGuard.
ReplyDeleteYou can use this to make any USB stick behave like a U3 drive, even using MD5 hashes to verify that your portable apps weren't injected with a virus when you used that stick elsewhere.
It can launch something appropriate to the drive or content immediately, or add relevant options to a menu to be presented to the user.
It also recognizes when a drive has been infected by an autorun worm, and can inoculate the drive in the way you've suggested.
Freely available at http://autorun.synthasite.com/AutoRunGuard.php
That leaves only one remaining excuse for not disabling autorun.inf files: Some Vista users may employ autorun.inf files to instruct AutoPlay to restrict its content searches in certain ways, and that's pretty minor.
Thank you Nick!
Dan
I'm facing exactly the same difficulties with autoruns as well. I liked your approach very much but I found your instructions rather difficult to follow.
ReplyDeleteShould I create a .REG file and double click it "execute it" and add the lines that will be in turn added to my main registry?
I'm sorry, but I'm still a clutz to editing the registry. If you help me out I'll be eternally gratified.
Yes. Copy the three lines which I posted into a file with the extension .REG and double-click it, then accept whatever dire warnings it gives you.
ReplyDeleteIf you see more than three lines, make sure that everything from "[HKEY_LOCAL_MACHINE"... through to "Autorun.inf]" is on a single line.
Good luck
Nick
Hi,
ReplyDeleteThis is great tip, but could you write how to go back to previous state, because some CD`s don`t work after install.
The equivalent file to undo the changes would be:
ReplyDeleteREGEDIT4
[-HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf]
Note the '-' character just after the left bracket.
But I'm not sure what you mean by "some CDs don't work". They certainly won't autorun - that's the idea - but you can always explore the root directory of the CD, open Autorun.inf in Notepad, and see what it does.
As soon as I find out, I`ll write it. It`s my college`s problem.
ReplyDeleteThanks for quick answer.
Sorry for my English mistakes, I`ve just started learn.
Hello again,
ReplyDeleteThere is license key and product number in Autorun.inf file.
It`s work now. Thanks.
Sorry to bring bad news but this technique is causing breakage on a new system.
ReplyDeleteI used it on a previous system but now it's:
a) disabling "Show desktop" and removing its icon from the shortcut
b) making Outlook 2003 complain "The extension C:\Program Files\Microsoft Office\OFFICE11\ADDINS\*.ecf could not be installed. There is an error in the syntax or format of the file." for each .ecf file
c) stopping Kaspersky Internet Security's firewall from fully starting.
This is on Windows XP Pro SP2 + hotfixes. Applying the technique causes these problems; removing it and restarting fixes the problems.
It should not make any difference but this WXP is running under VirtualBox 1.6.2 on unbuntu 8.04.
For more details see http://forum.kaspersky.com/index.php?showtopic=76418
Hi Charles,
ReplyDeleteWe don't have Kaspersky on our site but we do have Outlook 2003 and we have not seen the first two problems which you mentioned.
>>It should not make any difference
>>but this WXP is running under
>>VirtualBox 1.6.2 on unbuntu 8.04.
Perhaps it "shouldn't" make any difference, but my strong suspicion would be that it is doing. ;-)
Nick
Charles, you're putting the @="@SYS:DoesNotExist" in the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping key instead of the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf key.
ReplyDeleteThat might cause your problem. You have to create the Autorun.inf key.
Ooops! [FX: embarrased] My mistake -- that was the most likely explanation all along. Thanks to Anonymous (Joop) for finding it and pointing it out.
ReplyDeleteHello thx for the useful registery key
ReplyDeletebut i have a question
How to Configure this key Using Group Policy ??
>>How to Configure this key Using Group Policy ??
ReplyDeleteI don't know... I don't use Group Policy. :-) I presume you can add registry keys to the cute graphic layout. But I don't know if the code which applies policy reaches as far as IniFileMapping.
Microsoft finally offers an update to disable autorun completely, look here: http://support.microsoft.com/kb/953252
ReplyDeleteI'd seen that. But my version is (a) easier to understand, (b) immediately reversible, and (c) field-tested for over a year. :-))
ReplyDeleteHey - this looks like exactky what I need!
ReplyDeleteBut I am way behind on the required techy-ness...
I currently have the autorun worm on my laptop. The source was either a malicious download, or USB stick from my friend (both opened yesterday)
Before reading this article I just backed up my essential files - to a USB HDD (!?) and the USB stick is still in my computer.
My virus scan (AVG) is finding the worm on C:\ but I can't see this in windows explorer.
I believe that it is preventing me from accessing the internet even though I am showing as beiong connected local & internet on Vista.
I can't collect e-mail either.
How do I:
get rid of the autorun worm,
and
ensure thatthe 2 USB drives are not infected.
Your help is appreciated!!
BTW: I am not a corporate user, I'm a small business, so it's just me.
Steve,
ReplyDeleteI'm afraid I don't have a simple solution for you. This post is about preventing this sort of thing from happening. (Mind you, so was Vista. I guess Microsoft got it wrong in your case. Perhaps they'll pay for your PC to be fixed by way of an apology.)
If your a/v software can't remove it then you are going to need professional help. (Or rather, your PC is. I'm not suggesting that you need a doctor. :-)) If I were sitting in front of your PC I'm sure I could remove all traces of the virus in a few minutes, but there's no way I can teach you by mail all you'd need to know to do that.
In theory all you need to do is to delete the AUTORUN.INF file from the root directory of every drive in your system. But in practice, 90% of memory stick worms will have given themselves other automatic start points, so that won't be enough. And clearing up all the automatic start points in Windows is a huge subject in itself.
You should work on the assumption that every single USB memory device which you own is now infected. But then again, you should always assume that every USB device has a virus on it; that's why you need the preventive tips in this blog post.
Once your PC is cleaned up, apply the fix shown in this post (or, if you can't work out how to do it, show it to someone who can, such as the person who is going to clean up the PC). Then, you can safely put your USB devices into your system one at a time and clean them up with your anti-virus software.
Good luck,
Nick
Thanks Nick - good enough!
ReplyDeleteSomeone has already collected the computer and (apparently) are pretty clear on the issues as I was able to detail the extentof the damage thuis far.
Will inform them of this fix also.
BTW - great service. Not just fast, informative, convincing and believeable, but also funny! Especially given my rather dry post and the fact that I would expect responses to be court and clinical in this industry. Fantastic job!
Obviously it would have been better if you WERE sitting in front of my computer, or even betterif you could improve your ability to teach by email (i'm a quick learner)
...but can't ask for everything ;-)
Aw shucks. Can I give you my boss's e-mail address? :-)
ReplyDeleteHi Nick and everyone in the blog:
ReplyDeleteI'm from a small town in Argentina, with my brother have set a cybercafe (six PCs) your technique to prevent autorun is excelent, I can see you know a lot about this so I'll ask you a favor.
I want to put multimedia on shared folders but don't want people to steal those videos, images and audio.
With steal I mean I want they download their files from Internet consuming time that I can charge later.
At a first glance it will appear too mean to do this but I have to remember that it is a small town and for one hour the people in my cyber pay $ 1 (I only have 128 Kb connection -and, as you surely know, that's a nominal value, the little cents I do with the downloads are my incomes).
I thought up this idea:
the real files will be hidden at some folder
the files people will see in shared folders will be shortcuts
the shortcuts arrows will be erased from registry (so people will believe those are the originals)
My problem is that obviously they'll found out that the files are only 1 KB, so in the right click - properties to the file they'll found the root folder.
How can I disable this function from shared folders?
Most important: can you send me addresses to learn at least a small fraction of all you know?
You seam to be a technician with the registry, I'm reading an e-book about the registry from Jerry Honnycut (excellent, by the way) but your knowledge dazzles me.
I hope you can help me.
Thanks in advance...
I'm sure that most of what you want to do can be achieved with the registry, but I'm not really an expert. I'm a general "systems person" who's been programming and managing computers for over 30 years, but I've never really got into the whole Windows object model thing.
ReplyDeleteGood luck in your search
Nick
Thanks Nick for this post. Really informative.
ReplyDeleteJust wanna inquire though:
Will this also work for 2003 server,XP,vista or 2008 server? and I noticed the syntax you gave uses Regedit 4. Do we just use the same syntax for regedit 5.
Your response will be greatly appreciated. And would surely help lots of people.
(Sorry had to use anonymous - don't have an account yet. will set it up soon).
thanks!
-Bliss (Philippines)
Hello Bliss,
ReplyDeleteOn most systems, Regedit should recognise the REGEDIT4 syntax. Otherwise you can change the first line to "Windows Registry Editor Version 5.00" (without the quotes). Or open Regedit, export a key, and look at the syntax and paste the patch data as appropriate.
I'm assuming that this patch works on most versions of Windows. I use it on XP, and Server 2003 is basically the same code. Although why you would put a memory stick into a server is slightly beyond me. And of course there are no viruses or worms which affect Vista or later versions because Microsoft has made them totally secure (ha ha ha). That's why all the anti-virus companies have gone out of business (because nobody runs XP any more either, ha ha ha).
Good luck,
Nick
Hello. I'm not saying they've nicked your code, but have a look at this page: http://www.avertlabs.com/research/blog/
ReplyDeleteThanks for noticing that - someone else pointed it out to me last week, and I already send them a comment, which they haven't got around to publishing yet. :-/
ReplyDeleteStill, the US-Cert article to which it links mentions this blog. I'll also ask US-Cert to add my name and Emin's to the "Credits" section.
Just thought I'd tell you what the /?? prefix meant in the filename-
ReplyDeleteIt's used in the CreateFile() function, which is used to open any file, for the purpose of allowing filename lengths longer then the defined maximum previously used in Pre-NT operating systems.
Thanks for that - a mystery which has been bothering me (not very much...) for 12 years is now solved!
ReplyDeleteOkay, so i made the fle, gave it a ".reg" suffix, and double-clicked it.
ReplyDeleteWindows immediately asked me what program to use to open the file (suggesting EditPad Lite).
So what do i do? Do i need to save it in a perticular directory?
Running XP, SP3.
Mike,
ReplyDeleteWhen asked what program to use, browse to C:\Windows or C:\Windows\System32 and choose "Regedit".
Nick
How do I implement this hack using REGEDIT?
ReplyDelete.REG MERGE functionality is broken on my computer.
And it would just be interesting to see what it looks like in REGEDIT view.
Start Regedit. Go into HKEY_LOCAL_MACHINE, SOFTWARE, Microsoft, Windows NT, CurrentVersion. Right-click on "IniFileMapping" and choose "New"/"Key". Name the new key "Autorun.inf". Go into "IniFileMapping" and "Autorun.inf". Double-click "(Default)" (in the right-hand pane) and enter "@SYS:DoesNotExist". (Leave my quote marks out, of course.)
ReplyDeleteAfter implementing this hack as explained and attaching an external USB drive, the little AutoPlay window and subsequently the AutoRun window appeared.
ReplyDeletePlease correct me if wrong. This reg hack does NOT stop AutoRun / AutoPlay from working. It simply neuters any AutoRun.inf file on any attached device.
So the appearance of the AutoPlay and AutoRun windows after implementing this hack, are still expected. Is this correct?
Thanks
Yes, that's correct.
ReplyDeleteHowever, since is a substantial number of cases the required action on inserting the media - for example, autostarting the Setup.exe procedure on a software CD - is described by the Autorun.inf file, there will, in such cases, be a change in overall behaviour (you'll have to run setup.exe manually, or whatever).
Quite a lot of memory worms don't run anything directly when you insert the stick. Instead, they install (via Autorun.inf) a handler in Windows Explorer's "File" menu, which causes the worm to spread when you explore the drive.
hi
ReplyDeletethank you for posting a very good idea. i wanted to know, if u can kindly tell me, that actually most of the autorun and assosciated worm files normally hide themselves...is there any tool or registry way to make them unhide....so that i can delete them?
thanks for answering in advance....
There's no easy answer. If you have such a virus/worm, you'll probably find pointers to at least the first part of it in the Autorun.inf files which it will typically leave in the root directory of your hard disk partition(s). But many of these worms leave other things in other places. Look at programs like Silent Runners or Hijack This! for ideas on how to hunt down auto-running software.
ReplyDeleteI am trying to show the boss the danger of AUTORUN.INF
ReplyDeleteI created an AUTORUN.INF on a USB stick. I plug the stick into the USB port. The AUTOPLAY menu appears but executable does not execute:
[Autorun]
OPEN=AUTORUN.EXE
ICON=AUTORUN.ICO
The AUTORUN.EXE and AUTORUN.ICO files are on the stick.
This is a clean install of XP HOME with SP3. It does have Windows Defender and AVG Free on it but they do not show any alerts or events in the logs.
No idea... sounds like you're already protected somehow. :-)
ReplyDeleteDisabling Autorun
ReplyDeleteNumber: TR08-004
Date: 22 December 2008
http://www.publicsafety.gc.ca/prg/em/ccirc/2008/tr08-004-eng.aspx
"Sys:DoesNotExist" is the only Recommended Solution.
Mike
Sweet! Go Canada!
ReplyDelete@G Laverne Flambeau
ReplyDeleteContrary to on CD's/DVD's, the "Open=" command does not cause the app to start on insertion of the USB stick. Provided that NoDriveTypeAutoRun under HKCU has the default XP value of 0x91, and no value exists under HKLM, this should do the trick:
[autorun]
shellexecute=autorun.exe
useautoplay=1
Great work Nick.
ReplyDeleteCan you help with this scenario?
Say a person's system is running XP and has a virus scanner installed. Said scanner has a "scan removable media" function, and it's enabled.
Is that a reliable enough scanner to protect me and to not have to install your autorun hack?
If not, and a user chose to hold down the Shift key when inserting the media to prevent autorun, in what danger is that user now of an infection from USB stick?
You said, "Quite a lot of memory worms don't run anything directly when you insert the stick. Instead, they install (via Autorun.inf) a handler in Windows Explorer's "File" menu, which causes the worm to spread when you explore the drive."
Will a right-click on the drive in WinExplorer cause the worm to activate?
The concern is that if we bypass autorun successfully by some method to be safe, and then want to virus scan the USB device, will that "touch" of the device activate the nasty on there?
Thanks for all your great help!
Hi Buddy,
ReplyDelete>Is that a reliable enough scanner
>to protect me and to not have to
>install your autorun hack?
Only if your anti-virus scanner is updated to include every new memory stick worm before they arrive at your site. I haven't heard of any which claim to apply generic protection to removable drives.
We remove 3 or 4 viruses a week from our network, which we detect using a variety of home-brewed means. When we find a worm or infected file, we always submit to the superb site virustotal.com, which runs it past about 35 antivirus products. It's very common for only 10 of the 35 to detect it. So to have an 80% chance of catching the virus, you'd need to have five scanners on your system, each updated daily. How much was that migration to a Linux desktop going to cost you? :-)
>If not, and a user chose to hold
>down the Shift key when inserting
>the media to prevent autorun, in
>what danger is that user now of
>an infection from USB stick?
My understanding is that holding down Shift does work to prevent any Autorun function. But realistically, your users are not going to remember to do this in 100.000000% of cases.
>Will a right-click on the drive
>in WinExplorer cause the worm to
>activate?
Yes, that's typically how these viruses work. At that point the worm will copy itself to the root of all the drives on the system and install an Autorun.inf on there too. With a network drive shared by 500 people, you can have 500 copies on your LAN by the end of business.
Good luck!
Nick
I think I've found an easier way to prevent autorun. I just tried this on an XP Pro SP3 computer, and it worked when I tried it with a SanDisk. If there's anything wrong with this method, which is supposed to work on XP/Vista, please let me know.
ReplyDeleteGo to the following Registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Cdrom
Double-click on Autorun, and you'll see a default value of 1. Change it to 0 (zero). Then restart the computer.
After you go to all this trouble, don't double-click that autorun.inf file on the disk—it can still run if you do.
[Thanks to PC Magazine for this tip, which I found at:
http://www.pcmag.com/article2/0,2817,2254345,00.asp ].
Interesting. I'd expect this to have no effect on a device which is not being handled by the CD-Rom driver. Some research would appear to be indicated. :)
ReplyDeleteNick,
ReplyDeleteI also thought there would be
a problem with any device other than a DVD/CD, but as I said, I tried it with a SanDisk disk-on-key. When the value is 1, the U3 software pops up. When the value is 0, the U3 software does not pop up, but all the partitions, including the one containing U3 are still visible.
This method is easily reversible.
I read that Vista SP2 is going to correct this problem, making autrun not work by default, by I haven't yet had the opportunity to check the beta version and see if and how it's been accomplished.
I appreciate all the info-I'm a network chief cook/bottlewasher/genie/fire extinguisher so you've really cut short my work :)
ReplyDeleteBut there is one thing I haven't found any info on yet:
How does the worm get into the pen drive in the first place???
Thanks again!
It gets onto the pen drive because the pen drive was put into an infected PC. The pen drive then infects other PCs.
ReplyDeleteIf the pen drive is the chicken then the PC is the egg. And as everyone knows, the egg came first (the chicken is just a device for making more eggs), which in this case means that the first PC "infected" in the world was the one belonging to the person who wrote the worm.
Regarding use of Group Policy to apply registry changes, I'm attaching a sample script I wrote to enable PMTU Blackhole Detection and PMTU Discovery on Windows systems. The script was based upon a killbit script found through a link on the ISC - some residual comments remain. Saved as a command file in the netlogon directory the command file is executed as a startup script in Group Policy Computer settings. The script requires a parameter of "enable" or "disable" to set the values on or off. It could easily be modified to use the hack Nick posted above as well as the reversal hack should life go horribly wrong in your environment
ReplyDeleteScript follows:
@echo off
REM Print some debugging info
date /t >> %systemdrive%\PMTU.out
time /t >> %systemdrive%\PMTU.out
REM Start writing the header to our registry script
echo Windows Registry Editor Version 5.00 > PMTU.reg
echo. >> PMTU.reg
if "%1" == "" (
echo ERROR: You must specify either "enable" or "disable" on the command line for this script to have any effect >> %systemdrive%\PMTU.out
goto cleanup
)
if /i disable == %1 (
echo Disabling PMTU Options >> %systemdrive%\PMTU.out
REM Finish creating our reg file. This one sets the kill bit
echo [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters] >> PMTU.reg
echo "EnablePMTUBHDetect "=dword:00000000 >> PMTU.reg
echo [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters] >> PMTU.reg
echo "EnablePMTUDiscovery"=dword:00000000 >> PMTU.reg
REM Call the reg file
regedit /s PMTU.reg >> %systemdrive%\PMTU.out
goto cleanup
) else (
if /i enable == %1 (
echo Enabling PMTU Options >> %systemdrive%\PMTU.out
REM Finish creating our reg file. This one sets the kill bit
echo [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters] >> PMTU.reg
echo "EnablePMTUBHDetect "=dword:00000001 >> PMTU.reg
echo [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters] >> PMTU.reg
echo "EnablePMTUDiscovery"=dword:00000001 >> PMTU.reg
REM Call the reg file
regedit /s PMTU.reg >> %systemdrive%\PMTU.out
goto cleanup
) else (
echo ERROR: You must specify either "enable" or "disable" on the command line for this script to have any effect >> %systemdrive%\PMTU.out
goto cleanup
)
)
:cleanup
REM Delete the registry script
DEL PMTU.reg
echo Finished processing >> %systemdrive%\PMTU.out
echo. >> %systemdrive%\PMTU.out
echo ======================================= >> %systemdrive%\PMTU.out
> > Buddy Lembeck:
ReplyDelete> > If not, and a user chose to hold down the Shift key
> > when inserting the media to prevent autorun, in what
> > danger is that user now of an infection from USB stick?
> Nick Brown:
> My understanding is that holding down Shift does work
> to prevent any Autorun function.
XP: yes. However, under Vista this functionality was removed, see the bottom question at Microsoft's AutoPlay FAQ.
Nick, thanks for the trick, it worked for me. However, I have some weird news: I caught Downadup from a Linux machine. I dunno how, but I've sticked my pendrive only in Linux boxes today at a fair and got infected when I sticked it up in my laptop back home. Have you heard about it before?
ReplyDeleteFabio, attempting to trace where you actually got it from will be impossible. My guess would be either that Wine is getting very good indeed, or that maybe the Linux machine created a share on the stick and Samba was running. Or maybe your laptop was already infected (there presumably has to be a Windows machine in the chain somewhere).
ReplyDeleteOtherwise, I recommend this for light entertainment on a related matter: http://www.youtube.com/watch?v=xKZR3Bcj4jw :-)))
>> The second @ is part of the final value which goes into the registry. It means "what follows is a pointer - follow it".
ReplyDelete>> We want Windows to follow the pointer and finish up at a dead end, where it will say, "OK, this entire INI file maps to nothing".
Fair enough, however I am looking through a few dozen other "IniFileMapping" entries in the registry, and none of them starts with an "@". Some start with a hash (#), and some just say "SYS:...". Would you please provide a reference where you saw the "@" (at) symbol used before "SYS:" ?
Thanks in advance!
The various prefix characters are explained here: http://technet.microsoft.com/en-us/library/cc722567.aspx.
ReplyDeleteThe @ is completely essential to this fix. If you don't have it, since the registry key doesn't exist, Windows will read the Autorun file, which is exactly what you're trying to avoid.
The reason you haven't seen the @ character is because generally, IniFileMapping provides a way to set global values which override whatever is in the INI (etc; in our case, INF) file. If @ isn't provided and the file exists, then it will be read unless the corresponding value tag exists in the registry. Normally this is what you want, because normally you aren't trying to prevent stuff from happening. In the case which we're interested in here, without using @ you would have to provide registry values for every possible tag value that could appear in the Autorun.INF file.
Nick, thank you for the great tip. I tried the undo solution you posted above but I can't seem to get it to work. I copied the two lines into a notepad file and saved it as undo.reg, and double-clicked it to enter it into the registry. The autorun.ini file is still not being executed. Am I missing a step somewhere? I also rebooted.
ReplyDeleteHmmm. I suggest you open REGEDIT and navigate down to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping. You should not see a subkey ("folder") called Autorun.inf. If you see it, delete it. That's all the 2-line file does. And as far as I know, Autorun.inf should then work immediately, but certainly it should work after a reboot.
ReplyDeleteNick, thank you for the great work first. I have a question. What will happen if the HKLM\SOFTWARE\DoesNotExist key exists? Do you think there is a possibility for exploitation?
ReplyDeleteVlad, that's an excellent point. It would require an attacker to have previously had access to your PC to create that key. But if you want to be extra-secure, generate a random 32-letter sequence and use that in place of "DoesNotExist". Or, write a sentence which describes exactly what you think of Microsoft's attitude to security and use the last letter of each word of the sentence. :-)
ReplyDeleteI suggest showing exactly how this hack is supposed to look using a screen shot pic, as one views it in regedit. The @SYS and even the rest may leave some in an unknown or even false sense of security. A screen shot of the regkey would be very useful.
ReplyDeleteThe Cdrom thing I think is one of the MS suggestions, no? I've seen it before. I don't have it set to 0 now so my guess is I used it before elsewhere and it worked but forgot about it (I am using an MS hack now I'm sure), or it didn't work well enough for me to continue using it. I always have been concerned about the USB drive - I know my discs won't autorun, but I wasn't sure about USB. I could have but an autorun.inf on it, right - coulda/woulda/shoulda -> didnta.
continued:
ReplyDeleteP.S. I recall itunes having a problem recognizing changed CDs in the past when I had some sort of autorun hack in, and I think it was the above-mentioned Cdrom hack. I had to close/reopen itunes to get it to recognized a changed CD. That may be the reason I don't use the Cdrom hack anymore.
On further reflection, it would of course be even easier for an attacker to delete the IniFileMapping\Autorun.inf key - after all, there's a 2-line registry file to do it somewhere above this post. :-)
ReplyDeleteSo if you want to rely on this once the bad guys wake up to it, make it part of System Policy, or perhaps try and tie down the registry permissions so it can't be deleted (good luck with that).
I'll look into posting a screen shot. One problem I see with that is that to verify it against your system, you have to open Regedit interactively, and if you're sufficiently well-informed to do that, you should know what you're looking for. But maybe I'm being too picky.
ReplyDeleteA couple of people have suggested that I post the .REG file, ready to go. The problem there is that as soon as someone clicks it, I become responsible for every problem on their PC for the next year...
Thanks Nick, good tech tool to have to help to keep the infections down. If you get an infection, this fellow has a good cure.
ReplyDeleteI work at a college and we have been using this to keep our machines clean.
http://www.en.mygeekside.com/?cat=8
MAT
Nick, I played a little bit with the Autorun.inf key. First, I observed the permanent behavior change in the SanDisk Cruzer U3. After the key was applied the Cruzer started opening two Explorer windows, one for a CD-ROM emulation partition, another for a data partition. Double click on the U3 executable opened another Explorer window in the "...\Documents and Settings\{user-name}\Application Data\U3\{16-digit-hex-number}" folder. The behavior was very stable. Removing the MountPoints2 did not help. After the Autorun.inf key was removed nothing changed until the system was rebooted. Even after reboot the behavior was different than initially. The U3 application started as it should but on top of that the Explorer window popped up with the U3 data partition. I have no problem with that but just wanted to document that the Autorun.inf key introduction affects the U3 application even after the key is removed from the registry and the OS was restarted. What I have a problem with is that U3 application stops working when the Autorun.inf key is present. Second, I tried playing with the DoesNotExist key and observed some very interesting changes in double-click on autorun.inf behavior. I think your suggestion to try the registry permissions is very valid. Should probably be done on both keys. As you said, "the world is our beta site" ;)
ReplyDelete"and if you're sufficiently well-informed to do that, you should know what you're looking for"
ReplyDeleteCut-n-paste only works if you cut and paste it all. I left off trailing quote. Try it. Unless you know what it's supposed to look like, you don't know what you're looking at. It took me more than once (okay, about four times) to notice why I wasn't seeing the Default with any value.
Wow, this is really great!!
ReplyDeleteCan I translate it to Indonesian so I can give this information to my fellows Indonesian?
Terimakasih banyak! (Thanks a lot! in Indonesian)
Hi Rudra,
ReplyDeleteIt's no problem for me if you want to post a translation. Just please include a link to the original article.
Thanks,
Nick
Nick,
ReplyDeleteYour solution to the problem is great. To me, it's better, simpler and more ironclad than the assorted work-arounds from Microsoft. I wrote more about it on my Computerworld blog
The best way to disable Autorun for protection from infected USB flash drives
http://blogs.computerworld.com/the_best_way_to_disable_autorun_to_be_protected_from_infected_usb_flash_drives
And, I created a test autorun.inf file too so people can test whether their PCs are vulnerable to the assorted autorun.inf tricks.
Test your defenses against malicious USB flash drives
http://blogs.computerworld.com/test_your_defenses_against_malicious_usb_flash_drives
Hi..
ReplyDeleteThis looks great but quick query.. G: for my laptop is always my USB mobile broadband toggle, which kicks off with autorun.inf (triggers autorun.exe), and obviously I still want that to happen..
Without trying it first, will this overall fix generally then render the broadband toggle mute on start up..?? I don't want to have to physically run this each time..
Alternatively, does the autorun program guard (haven't looked at it) allow more control in this direction (ie allowing g: to work but blocking the rest of the drives, for example?)
Many thanks..
Peter
Peter, I'm afraid you're going to lose that functionality if you apply this patch. Try creating a shortcut to G:\AUTORUN.EXE on your desktop and double-click that when you put the mobile broadband key in the PC.
ReplyDeleteAlternatively, you could build a REG file which undoes the Autorun.inf hack before you insert the key and another which puts it back afterwards, but that's even more clicking.
Hi Nick,
ReplyDeleteThat's interesting.. the desktop shortcut sounds like the obvious route with this, if keeping sound control. Actually it seems a lot more intuitive in any case; it reminds me of a time when everything was not in dumb down mode!!
Many thanks for your help...
Regards,
Peter
Nick, please help!
ReplyDeleteI have my USB infected with Win32.Virut.Q. I want to format my flash USB drive but I don't know how to do it without infecting my computer. Although, you showed me how to avoid automatic infection I will still infect my computer if I right-click the flash drive in order to format it. I tried to do it from DOS but DOS doesn't see the USB drive at all. Is there any way to format my hard drive, or should I start looking for a new one? Thanks in advance.
It sounds like your best bet would be to find another computer (with the @SYS:DoesNotExist patch installed) and clean up the USB stick on that. Then use a free anti-virus tool to clean up your PC.
ReplyDeleteSomething else which might just work is to open a command prompt, go into the memory stick (say E:) and run these commands:
del /a /f \autorun.inf
md \autorun.inf
echo x>\autorun.inf\a.txt
(Most viruses won't delete a directory called autorun.inf in order to create the file with the same name.)
Good luck
Nick
Thanks for your help. Fortunately, it wasn't my computer that infected my flash. It was infected when I plugged it to my friend's computer. I haven't plugged my flash into my computer ever since then because I was afraid that I might infect my computer too.
ReplyDeleteI have some old computer where I can install this @SYS:DoesNotExist patch. But to format flash, I have to right-click the drive in Windows Explorer and I am afraid that in that very moment virus may spread to that computer too. Am I right or there is no danger of such scenario?
If the @SYS:DoesNotExist patch is installed, the virus's Autorun.inf file will not be used. So you should be OK.
ReplyDeleteOf course, you could also format the memory stick by opening a command prompt window and using the FORMAT command. :-)
Thanks Nick. I'll give it a try and let you know how it went.
ReplyDeleteHello; I'm pretty new at this and I'm not sure where I'm supposed to type those 3 lines you were talking about. Could you help me out? Thank you in advance
ReplyDeleteHi CF6-50,
ReplyDeleteI'm not able to explain it any more simply than I already have. But if you go to http://blogs.computerworld.com/the_best_way_to_disable_autorun_to_be_protected_from_infected_usb_flash_drives then you will find a much more detailed description.
Good luck,
Nick
Dear Nick,
ReplyDeleteJust a word of Admiration and Appreciation. I Admire and Appreciate your Willingness and Dedication towards helping all these people. Great job. Please keep it up.
Mohammed Imtiaz
Wow, this is a really clever trick. Being able to block autorun.inf without completely killing AutoPlay is great.
ReplyDeleteI'm primarily posting to dispell some needless fear: simply right-clicking a drive with menu entries added via the shell entries in an autorun.inf will not execute anything. Of course, these entries can set a new default action for when you double click the drive (like has been mentioned) but if you right click the drive, you'll simply be presented with the standard actions plus any defined in an autorun.inf.
As to why disabling autorun for CD drives affects some Sandisk flash drives... they emulate a CD drive to use the completely automated autorun capability CD drives are typically allowed. A Sandisk Cruzer modified to automatically run something malicious is far more dangerous than a standard flash drive since no user interaction is necessary to launch the autorun specified entry from the emulated CD drive (under default conditions).
Queue
This is very cool; Microsoft has finally done something about the autoplay/ autorun problem. KB967715,
ReplyDeletehttp://support.microsoft.com/kb/967715 which I got yesterday as a critical update, adds full registry support for disabling these functions! Better late than never I guess.
OK guys and gals, let's get testing. I'm especially interested to see if this MS update overrides the "MountPoints2" key, which maintains "handy" cached information about removable devices which the system has already seen, presumably because they can be trusted (ha).
ReplyDeleteThanks for getting this out there, Nick. To make it even easier for people, I created a downloadable script per your instructions and have it hosted on pcworld.com. It's at http://www.pcworld.com/downloads/file/fid,76805/description.html, with a script to re-enable Autorun at http://www.pcworld.com/downloads/file/fid,76806/description.html.
ReplyDeleteCheers,
Erik Larkin
Thanks Erik!
ReplyDeleteI notice your article says that this improves security "on Windows XP". I'm pretty sure it works on Vista too. :-)
Nick
Thank you thank you for a solution that seems to have solved my problem! Made a rookie's mistake, attached an unkown USB. Even though I do all the other Windows best practice stuff- limited profile, etc, I also had autorun enabled... AND I auto-transferred my pix to my comp using SONY software. Well have promptly uninstalled that.. I use Windows XP home, and have Windows firewall and avast antivirus home edition, cos I'm cheap, but that had served me well until autorun inf. I guess my camera is now infected,.. Anyway I used the solution at
ReplyDeletehttp://bleuken.i.ph/blogs/bleuken/2007/06/29/viruses-that-uses-autoruninf/
but wasn't really getting any joy within the windows profile I was using when I got the infection.... I also tried to disable autorun as this site advised
http://ask.metafilter.com/97107/XP-Filter-I-set-up-a-non-admin-account-for-safer-computing-Am-I-safe-enough-now
but as you point out it has to be done for each profile... And that was just a pain, and I wasn't really sure it was working for me. AND I couldn't seem to get the worm off my memory stick. Your solution has finally shut up avast, and I guess nothing else is going on, so I am very grateful! Only two minutes of browsing and one minute of work! I did check my system files as soon as I realised I had infected my comp, have been checking if any look suspicious (hmm hard to tell) or if any have been modified since the infection, and so far I can't see any other evidence. That pesky autorun inf thing which has gone quiet. I hope that means I'm safe....
That "bleuken" blog fix fails to take into account the "MountPoints2" caching, which means that it might prevent Autorun from other people's memory sticks, but not your own. And most people only put their own sticks in their PC; after all, that's "safer"...
ReplyDeleteOh ok... that sounds complicated :) Well I found something weird after I left my comment- have posted about it over at my blog, also put a link to this post... http://shonatiger.blogspot.com/2009/02/object-lesson-autoruninf.html
ReplyDeleteThanks again Nick. Just hoping I closed all the holes... Because I'm not a pro at this, was feeling quite harassed... :)
hi Nick
ReplyDeleteits really nice trick there
I am using another trick to protect my usb flashes and even all hard disks from being infected by autorun viruses
by creating a folder called autorun.inf and making it undeletable (at least to 99.9% of the malwares out there)
anyway the trick to create the undeletable folder on a drive is: (assuming the flash drive letter is x:)
md "x:\autorun.inf"
type nul > "\\?\x:\autorun.inf\lpt9.Protected_By_kOuD3LkA
attrib +R +S +H "x:\autorun.inf"
and thats it
the file
lpt9.Protected_By_kOuD3LkA
is undeletable by simple means (using explorer or normal del command)
and this way if you connect the flash in another infected computer the virus will not be able to delete the folder and put its autorun.inf file (it can put the virus executable however but it will not be active since autorun.inf is not there)
Hi kOuD3LkA,
ReplyDeleteNice idea. I already blogged it on 25th October 2007, a couple of days after publishing the hack under discussion here. :-) But I can't say for sure if I was the first person to think of it.
Nick
Hi Nick, I find your way is the best to disable autorun. Thus, I have created a program here with other features. http://raylin.wordpress.com/downloads/autorun-protector/
ReplyDeleteI tried this on my Windows XP machine, but autoplay still runs.
ReplyDeleteMy registry doesn't look like your screenshot. There's nothing like
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping
I see HKEY_LOCAL_MACHINE\SOFTWARE\ but there is no "Microsoft" sub-directory underneath.
Suggestions?
If you can't go below HKEY_LOCAL_MACHINE\Software then something is wrong, either with REGEDIT or maybe your privileges.
ReplyDeleteThis hack does not stop AutoPlay from running. It just stops Windows from opening Autorun.inf files. Autorun and AutoPlay are totally different things, even if only 0.1% of Microsoft staff could tell you the difference.
hello nick
ReplyDeleteearlier i had asked you about some way to see hidden files. i happened to find a little way. if you open the stick using winrar which is normally available, it displays all the files and folders. if you knew what was there in your stick, you can easily figure out what are the culprit files.....just delete them...and enjoy......
Hi Nick - Created the reg file
ReplyDeleteand could not see the usb stick.
great !!! Then created the reverse
file and could still not find the stick. even after re-boot.
Thx Annon
Then you have broken something else: the USB storage driver, or some other component of Windows. Nothing about this fix would prevent USB storage from being seen, except that of course once you're clicking in the registry, anything can happen. I sympathise, but I don't think I can help much more here.
ReplyDeleteNick
Nick, did you know your work has been cited by the gov't?
ReplyDeletehttp://www.us-cert.gov/cas/techalerts/TA09-020A.html
They suggest using your solution over Microsoft's
Yep, I'd seen that. Funnily enough, President Obama is in my town this weekend. But I didn't get an invitation from the ungrateful @#!$%. :-))
ReplyDeleteI was trying to use the 'official' NoDriveTypeAutoRun = 0xFF approach on vista(with 950582 applied) and even when I cleared out the existing entry for the usb drive under mountpoints2 it was still processing autorun.inf for some strange reason.
ReplyDeleteAnyway Nick, this blog entry of yours saved the day. Just wanted to say Thankyou.
Apparently you need patch 967715, which finally fixes this. But judging by the traffic to this blog this week (11,000 users since Monday), not everybody has got the message from Microsoft yet...
ReplyDeleteAccording to the table at the top of http://support.microsoft.com/kb/967715, 950582 is the vista equivalent of 967715 (XP, Server 2003, 2000 only). Maybe I wasn't clearing mountpoints2 out properly.
ReplyDeleteI'm not so sure it's people "not getting the message", I suspect that they just feel more confident in your workaround.
Anyway, Nice to hear you getting all that traffic. It must be gratifying knowing you've helped so many people.
FYI: Something not mentioned yet in this sea of comments :) is the "REG" command, which can be used to do this with a single command line (useful, e.g., in a batch file). The command is:
ReplyDeleteREG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf" /ve /t REG_SZ /d "@SYS:DoesNotExist" /f
That's all one line; watch for wrapping.
Unrelated FYI: I've seen mention of this blog post in several notable places, including Canada's CERT equivalent. I cite it every chance I get. I saw this here way before I saw it elsewhere. So good work!
The reason I didn't give the REG command is probably the same as the reason that the copy-and-paste file uses REGEDIT4: I'm old. I was already too old for this game when I had to drop VMS and learn NT4.0. So I just learned the tools I needed to get the job done.
ReplyDeleteI used a version of REG.EXE in the NT4 resource kit for a while. I even had a few .BAT files which ran "REG bla bla" commands, because \NTRESKIT was in my path. Then XP came along with REG.EXE as standard and everything broke, because the syntax changed (radically). I'm just about now picking the last of the chewing gum out of my hair on that one.
And don't even get me started on the kind of crappy application software that thinks it's adding itself to the path (guys: check out component registration, m'kay?) but manages to "update" the PATH registry entry with a REG_SZ instead of a REG_EXPAND_SZ, so your logon scripts no longer run correctly.
Anyway, thanks first for your astute and insightful FYI. :-) Feel free to tell your friends to visit the blog and maybe even click on the ads :-). But for goodness sake don't go any further, because as far as I can see, 95% of them are for fake anti-virus software...
Nick
Nick,
ReplyDeleteJust ran into this and it's a gem. Thanks for making it available.
I have one question. Most of the clients at the Hospice I support access their applications via Citrix XenApp 4.5. Does it make any sense to apply this patch to the servers?
The way folks access is via PC workstations that run an ICA client that then logs onto the Citrix server farm. We do not allow drive mapping. I plan to implement this on the local workstations.
TIA for your feedback and again, thanks for the patch..
Hank Arnold (MVP)
Hank,
ReplyDeleteI'm sorry, I don't know anything about the Citrix environment. It would depend on how the client registries are instantiated. Maybe you should even be applying it to the servers and *not* the clients, although I'm guessing that's not the case.
This patch is fairly innocuous and reversible, so it shouldn't hurt to apply it anyway. (After all, the system managers maybe use USB sticks too.)
You can see if the patch is working by creating a trivial autorun.inf file like this:
[autorun]
open=notepad.exe
and then putting the USB stick into the PC, and seeing if Notepad opens.
Good luck,
Nick
Installed your patch and restarted my XP pro (on a PC within our LAN) but when inserting the USB it would still autoload/autorun as if nothing happened.... :(
ReplyDeleteAnd we don't have any group policies running at startup to wipe out entries and installed hack as Admin.
Joe
If you mean that when you plug the stick in that you still get "what do you want to do with these files" and maybe an Explorer window opening on the root of the drive: that's normal. That's Autoplay, which has nothing to do with Autorun. (Of course, the two terms are massively confusing; even many Microsoft people don't know the difference.)
ReplyDeleteIf you have applied this patch and Windows is continuing to take notice of the content of Autorun.inf files, then probably you haven't done it quite right. But everything else, including Autoplay, should work like before.
Hi Nick,
ReplyDeleteI love your solution and have a quick question for you. SysDoesNotExist disables the U3 launchpad, have you heard or found a solution to disable autorun but still allow a user to manually launch the U3 lauchpad? Any suggestions would be great.
Thanks!
I have no idea what a "U3 launchpad" is. But if you look through some of the other replies to this post, "U3" appears there somewhere.
ReplyDeleteNick
Great tips from all, and thanks to Nick. Re: the tip frpm kOuD3LkA, I have been using a similar trick on my thumb drives; you can use lpt0-9 as well as CON and some other reserved keywords to make the subdir difficult to delete or overwrite. But I wanted to share an experience I had fighting a nasty virut infestaation - these bugs will treat ANY drive other than the main partition as a mountable removable volume, including a secondary partition, and I found out (the hard way) one possible outcome of creating a "decoy" autorun.inf folder off the root of a secondary partition to block the dropping of a malicious autorun.inf file: a bluescreen on bootup.
ReplyDeleteIt did help me flush out the last remnants of virut hiding in that secondary partition, but not until after giving me a few more grey hairs that I didn't really need.
Hi Nick! 1st of all, a zillion thanks to you for writing this blog post-it helps me from formatting my computer. BTW, i need some advise from you about this situation - i'm using WinXP Pro sp2, and using their auto-update, mine have updated to sp3. i've already disabling the autorun before the sp3 installation, but now, when i want to view it again (after upgrading), this occurs: 1, multiple warning appears (http://i245.photobucket.com/albums/gg69/m2mdoh/m2md%20blog%20stuff/gpeditprobs.jpg); and 2,after clicking 4times on that, the menu's under admin template has gone too~~ (http://i245.photobucket.com/albums/gg69/m2mdoh/m2md%20blog%20stuff/gpeditprobs2.jpg). now, i can't find the autorun under the system folder. Thanks again for your time and great help.
ReplyDelete.: m2mdoh :.
Sorry, I think you need a GPEdit expert. That's not me. I don't trust registry edits that I didn't apply myself and which I can't verify by booting from another system root. :-)
ReplyDeleteGood luck,
Nick
Hi Nick, thanks for the advice. I generally try to avoid messing with my registry though. How is your solution different from the following, which can be done through a normal windows xp route?
ReplyDelete1. Click Start > Run
2. Type “gpedit.msc”
3. Computer Configuration > Click “Administrative Templates” > Click “System” > Double-Click “Turn off Autoplay”
4. Setting tab > Check “Enabled” > Select “All drives” from the drop down menu > Apply > Ok
I got these instructions from this website:
http://www.llbbl.com/2006/06/13/how-to-disable-autoplay/
Because that is AutoPlay, and this is AutoRun. Read the rest of the comments here to get an idea of the difference. They are two totally different things, with similar names thought up be similar marketing folks. ;-)
ReplyDeleteFYI we've noticed that this method of disabling autorun prevents the use of Kingston's DataTraveler Secure Privacy Edition encrypted USB disk too.
ReplyDeleteNick, toward the top here was a tip for re-enabling AutoRun that added a - just inside of the left bracket. It did not say whether the third line would still be included or would be left out as well. Which would be advised if someone wanted an "undo" for the AutoRun undo?
ReplyDeleteThe file to undo this hack just consists of two lines, although I suspect that if you just added the '-' in the second position of line 2 and left the third line in place, it would still work.
ReplyDeleteHi Nick,
ReplyDeleteI was recently infected with a worm; the origin of which has not yet been determined. I am planning on zeroing my hard drive in the next week or so. After that, will it be safe to plug in my flash drives with known infections in order to try to clean them with antivirus software or should I just throw them out? How can I be certain that the antivirus software I have (Windows Live OneCare) will be effective?
Also, I just plugged in my digital camera flash drive today and realized that it is also infected. Does this mean that my digital camera hard drives are infected? If so, how on earth will I remedy that?
Thaks so much,
Ryan
...I alsmost forgot. The worst part about this is that I always have a 250 GB external USB hard drive connected to my computer which I am of course using to backup all of my data. Is it infected as well? In other words, will it simply reinfect my computer upon reconnecting it to my reformatted computer?
ReplyDeleteHello Ryan,
ReplyDeleteFor most memory stick worms, reinstalling the PC from scratch is probably excessive.
My suggestion would be to clean up your PC. That's beyond the scope of this reply; try AVG-Free or "Housecall" from Trend Micro.
Then, apply our registry hack, and you should be able to plug your removable media in without them infecting you. Go to the Autorun.inf file on each removable drive, open it in Notepad, note the names of the executables, delete those, and delete the Autorun.inf file itself.
Another option to delete the virus from removable storage is to plug it into a computer running anything but Windows and delete Autorun.inf from there. ;-)
Good luck,
Nick
This is a brilliant idea. Thanks nick and team, keep up the good stuffs. The world should thank you. ;)
ReplyDeleteMany thanks to Nick - someone asked me this below, can anyone help please ?
ReplyDeletewith this tweak if you double-click a drive (like CD drive)
in Explorer any autorun.inf on a CD in there gets executed despite the tweak ?
Double-clicking an INF file just opens it in Notepad, or whatever other action you've defined. It's not related to the issue discussed here, as far as I know.
ReplyDeleteYou could also just, er, try it and see what happens...
dear nick,
ReplyDeletefirst of all many thanks for an excellent article. i was especially impressed by the way you replied to all these questons, and even stayed polite if people asked things over and over :).
after travelling for one year and getting infected pretty much everytime i grab picures of someone i always got infected - a pain in the ass i can tell you.
i did read your whole article and all posts, leaving only one question for me to ask:
on a computer without your regtrick added, doublecklicking or opening the drive triggers the virus - i know first hand. but:
what, if i open "my computer", then swich to folder view (view | explorer bar | folders), then open the drive by only klicking on the little plus next to the drive letter on the left side of the explorer window (or highlighting it with mouse or keyboard, then pressing the "right" key instead of enter)?
thanks in advance, keep up the good work,
dennis (currently in thailand)
It was extremely interesting for me to read this blog. Thanks for it. I like such topics and anything connected to this matter. I would like to read more soon.
ReplyDeleteOn XP Home SP3 without your fix, but with the Microsoft anti-autoplay patch in place and activated, something odd happened the other day. I'm not sure why but I think I know how: removable media and hard disk started up autoplaying again, if only to open Windows Explorer or a choose-the-action dialog.
ReplyDeleteIt appears to me now that a NoDriveTypeAutoRun entry under HKEY_LOCAL_MACHINE causes the documented HKEY_CURRENT_USER setting to be ignored. A value of 0xb1 seems to have appeared there by itself. Going by the following table,
0x1 or 0x80 Disables AutoRun on drives of unknown type
0x4 Disables AutoRun on removable drives
0x8 Disables AutoRun on fixed drives
0x10 Disables AutoRun on network drives
0x20 Disables AutoRun on CD-ROM drives
0x40 Disables AutoRun on RAM disks
0xFF Disables AutoRun on all kinds of drives
- that meant that "fixed drives" and "removable drives" would autoplay.
http://support.microsoft.com/kb/967715
I don't know where that value came from. My recent operations include connecting a USB hard disk - apparently a "fixed drive" - that may have been registered in MountPoints2 previously, creating, deleting, and re-lettering partitions on the internal hard disk, and running a virus scanner from a Linux bootable CD called SystemRescueCD whose latest version apparently turned stable during the Christmas holiday. I've been soulsearching over that one, it's a popular tool that would be a good way to introduce a virus instead of detecting them, but a Linux-borne virus that bothers to interfere with Windows registry security settings and that causes visible changes of behaviour seems unlikely. Then again I believe SystemRescueCD is made by a French person :-)
For the Autorun.inf countermeasure described here... I think it would be an interesting refinement if it could be made to display a message such as "Execution of Autorun.inf on device E: was prevented using a clever remedy invented by Nick Brown. Press Escape or something." Well, something like that. That probably would require, at least, creating the registry key that in the current design is non-existent. Of course if Microsoft lets you disable AutoPlay entirely then you'll never see that, but... see start of my story!
Hi Robert,
ReplyDelete>removable media and hard disk
>started up autoplaying again,
>if only to open Windows Explorer
>or a choose-the-action dialog.
Do you mean "AutoPlay(ing)" or "AutoRun(ning)"? Two different things, although I doubt if 2% of 'Softies could tell you the difference. :-)
That said, it wouldn't surprise me if MS's workaround didn't work. For one thing, MS are notorious for not using their own APIs for a lot of stuff.
>if it could be made to display a
>message such as "Execution of
>Autorun.inf on device E: was
>prevented using a clever remedy
>invented by Nick Brown.
Heh, nice idea, but then I'd have to build a kit and ship a DLL. You should see the amount of trouble I have convincing people to add a one-line registry patch - I've seen loads of forum discussions where people who fancy themselves as experts dispense advice like "oooh, it modifies the registry, not worth the risk". I think they should fire up REGMON and see how many times every app in creation modifies the registry per second...
Nick
This trick is not working with Windows 9x?
ReplyDeleteWow. People are still running Windows 9x? I don't know if the hack will work. But in any case, I'm guessing that most modern worms won't work with Win9x anyway. ;-)
ReplyDeleteThanks for the tip Nick! :)
ReplyDeleteA question that I have is, can I copy this article? I wouldn't mind having this info on hand, in case I'm working on somebody's computer and I need to apply this patch.
Thanks again!
P.S. What is your policy concerning the copying of your articles?
Yes, copy it anywhere. It's on the Internet, so I assume it's everywhere. :-))
ReplyDeleteHi Nick,
ReplyDeleteI learn a lot of your tricks but i have a question, does this method can apply also on windows 7? any modification alteration or whatever needed instruction to be follow?
thank you very much
More power
I haven't seen Windows 7... I would have hoped that the official Microsoft way of doing things would be sufficient, but I'm going to guess that this hack might work. If it doesn't, it probably won't do any harm, anyway. Let me know if you test it.
ReplyDelete